Modifying Behavior to Protect Systems in a Malicious Threat Landscape
Credit to Author: Aaron Larson| Date: Wed, 01 May 2019 04:00:40 +0000
The malicious threat landscape for industrial control systems (ICSs) is constantly evolving and getting more sophisticated, thereby raising the need to have visibility, implement protective controls, and perform continuous monitoring. As a result, it is important to take a look at the attack vectors of some malware/malicious events—such as Triton—that have occurred over the last decade (Figure 1), including some attacks that did not target ICSs.
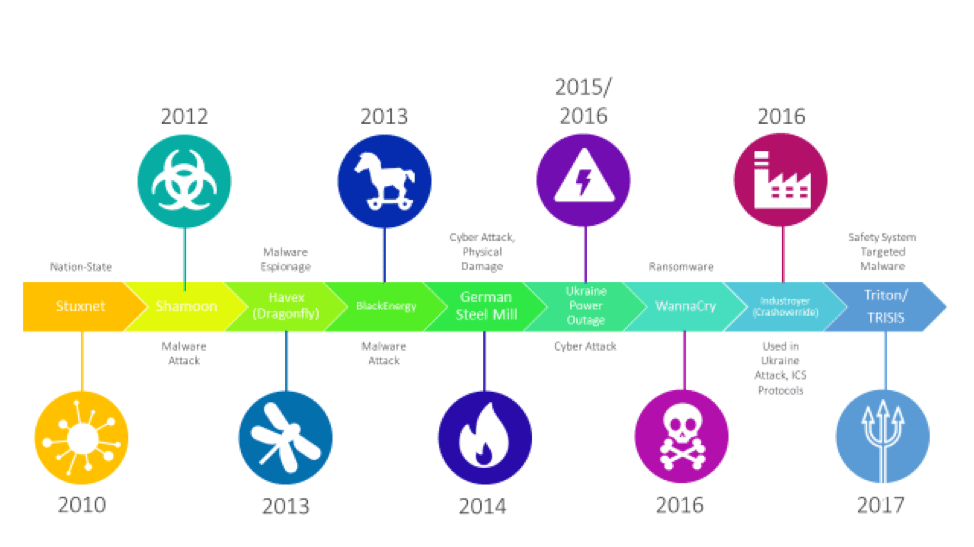 |
| 1. This timeline shows several cyberattacks that have created havoc in the past decade. Courtesy: Tripwire |
Whether it be ransomware, malware, or a targeted attack, each of these vectors need access to the environment. There are many ways for attackers to gain access; these events oftentimes involve phishing, stolen credentials, hijacking/infecting a transient device such as a laptop or USB flash drive, or exploiting a vulnerability, to name a few.
While NotPetya and WannaCry had a massive impact on industrial environments in terms of negatively impacting productivity and financial results, these threats did not directly target ICS environments. It is still very important to have visibility within a control network to understand if such an event is occurring, and it’s essential to have protective controls in place that can mitigate their spread and potential impact.
Anatomy of a Cyber Attack
If malicious behavior that could compromise an industrial process is analyzed, the same best practices around visibility, protective controls, and continuous monitoring apply. They can help organizations detect malicious activity before a threat actor gains control of industrial processes.
It’s important to remember that attackers first need access to the environment, which can be achieved by the following:
- Obtaining a network communications path, that is, “the way in” or “north-south traffic.”
- The existence of a vulnerability or configuration weakness (such as default passwords).
- An exploit to take advantage of a vulnerability and thereby gain access to the network communication path.
Once access is achieved, bad actors typically perform discovery or reconnaissance on the environment to plan how they will eventually take control of something so that they can execute the damage phase. They will then try to remove evidence of their attack.
In all of these phases (Figure 2), the one that takes the longest is the discovery/reconnaissance phase. Because it takes the longest, it gives those tasked with protecting industrial control environments the best chance to “see” that there are adversaries roaming around their industrial control networks looking to cause harm.
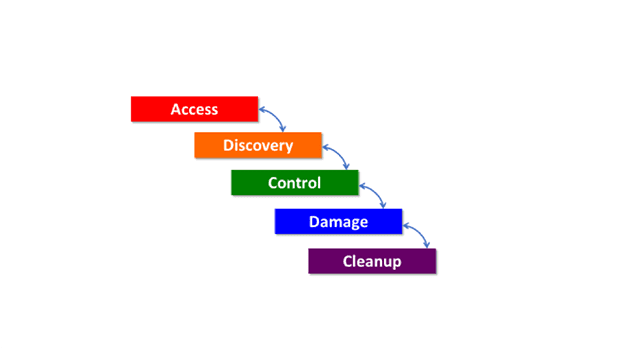 |
| 2. The flow path outlined here shows the phases of infiltration for a malicious “payload.” Courtesy: Tripwire |
In the BlackEnergy attacks that affected Ukraine in 2015, the threat actor performed discovery for at least six months learning about the environment. That’s right, at least six months. During this time, they gained access to the business IT network, pivoted to the industrial control network, and continued doing additional reconnaissance to learn as much about the environment as possible by looking for devices they could control to execute the damage phase.
In this case, the damage phase involved remotely taking control of breakers in substations, which ultimately resulted in a power outage. This behavior went undetected, inclusive of the summary of events and activities outlined below:
- The digital attackers gained access to the business/IT network via phishing emails.
- The bad actors embedded BlackEnergy3 malware into Microsoft Office documents—malicious files that led to the theft of user credentials via keystroke loggers.
- With user credentials, digital attackers achieved remote connectivity via a virtual private network (VPN). They were able to move laterally within the environment, that is, “east to west,” and blended in as “authorized” users.
- These malefactors then gained access to a separate network where uninterruptable power supplies were scheduled to be disconnected during the outage, making power restoration more difficult.
- They hijacked human-machine interfaces (HMIs) and supervisory control and data acquisition (SCADA) systems, and leveraged the HMI assets to open breakers in the substations.
- At that point, the attackers targeted field devices in substations. They uploaded malicious firmware to serial-to-Ethernet converters that disabled remote operation of devices in the substation.
- After performing an automated denial-of-service on call centers, the bad actors made Windows engineering workstations and SCADA servers inoperable with KillDisk—wiper malware that removes the master boot record from the system—so they are unable to be rebooted.
Mitigating Cyber Threats
How might this situation have played out if there had been visibility into the above behaviors? Organizations might have observed the following abnormalities:
- More users logging in through the VPN from non-normal remote locations and probably during non-normal times of the day.
- Firmware being uploaded to a number of serial-to-Ethernet converters in the substation.
They also might have recognized the following threats:
- Identification of command and control traffic from the propagation of malware.
- Identification of all the engineering workstations infected with BlackEnergy3 malware.
- Identification of KillDisk’s installation on Windows workstations and SCADA servers.
In its analysis of the event in Ukraine, the Electricity Information Sharing and Analysis Center (E-ISAC) provided several recommendations.
It suggested networks should be segmented, including between the business IT network and ICS network, between substations and the control center (north-south traffic), and within the substation and between substations (east-west traffic). The E-ISAC said end-users should ensure that device logging is enabled. Device logs can provide valuable information relative to what the device is doing and how it is operating, such as if firmware was updated or if someone tried to brute-force attack an administrator’s password. These logs can act as a forensics engine relative to cybersecurity incidents and operational concerns.
In addition, E-ISAC advised leveraging managed switches to provide additional information through the use of mirror ports and device logging. It said vulnerabilities should be prioritized and patched. For example, identify high-critical cybersecurity vulnerabilities that need to be remediated, and patch, if appropriate, or implement protective controls to mitigate the risk until a patch can be applied.
The center also suggested monitoring high-value systems, such as engineering workstations and servers. It said to leverage file integrity monitoring tools to identify changes, who made the changes, and whether changes were authorized or expected. Additionally, monitor these systems for adherence to a cybersecurity configuration guideline, such as IEC 62443 or NIST SP 800-82, and remediate when configuration evaluation tests fail.
Inaction Is Risky
These threats are real. Whether it’s unintentional from ransomware like WannaCry or intentional from direct targeted attacks like the one in Ukraine, cyber is and will continue to be a battlefield in the future as more and more devices are connected to industrial networks. Events from the last 10 years are a call to action and behavior must be examined. Make plans to enhance visibility, deploy protective controls, and continuously monitor the environment, because it’s only a matter of time for the next piece of malware to run rampant through industrial environments or for an adversary performing long-term reconnaissance to cause harm.
—Gary DiFazio is strategic marketing director for industrial cybersecurity with Tripwire. He has been in the technology space for more than 25 years, spanning experience with systems, applications, networking, and cybersecurity through a number of industry verticals including retail, industrial, federal government, financial services, utilities, and logistics/distribution.
The post Modifying Behavior to Protect Systems in a Malicious Threat Landscape appeared first on POWER Magazine.