Apple’s New Bug Bounty Is a ‘Historical Moment’ For the iPhone’s Security
Credit to Author: Lorenzo Franceschi-Bicchierai| Date: Wed, 14 Aug 2019 18:24:43 +0000
Last week, Apple announced that it was going to pay up to $1 million—even $1.5 million in certain circumstances—to friendly hackers who report vulnerabilities in the iPhone’s operating system. The company also announced that it will give select independent security researchers special “pre-hacked” iPhones so that they can look for flaws in iOS. Finally, it announced that anyone can report bugs to Apple through the program, not just people who had previously signed for and been approved for it.
The company’s head of security engineering Ivan Krstic made these announcements at the Black Hat security conference on Thursday of last week. What he didn’t say is that this is a major win not only for iOS hackers and jailbreakers, but also for users—and ultimately even for Apple.
“It’s a historical moment for iOS security,” said Luca Todesco, one of the most well known and respected independent iOS security researchers. “The bounty program now reflects more of the reality that advanced attackers face.”
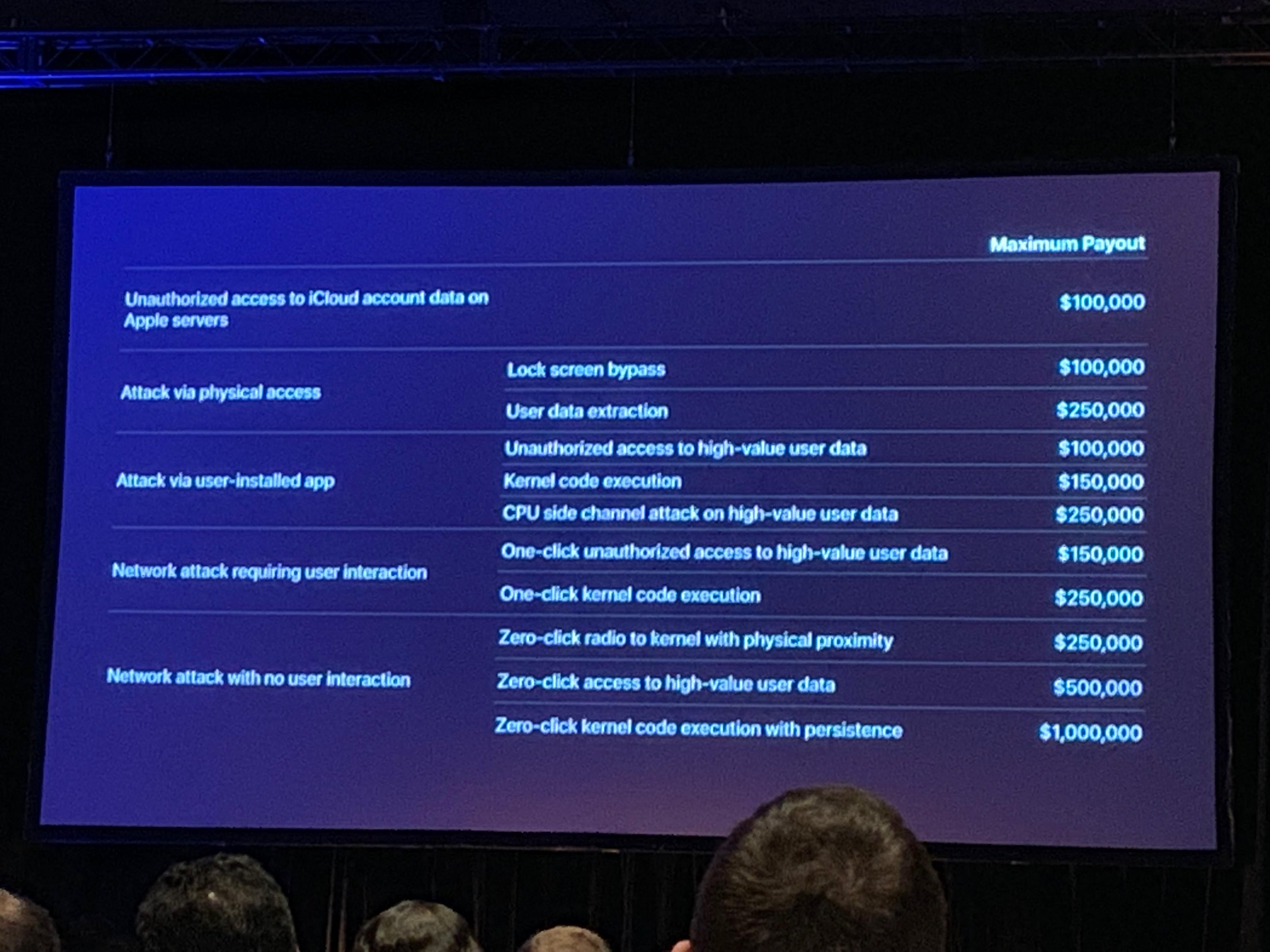
Todesco said that Apple’s new bug bounties can now “directly compete” with the secondary market for iOS flaws, which has been booming in the last few years, ever since vulnerability broker Zerodium announced in 2015 that it was willing to pay $1 million for a chain of bugs that allowed hackers to break into the iPhone remotely. Since then, the prices have skyrocketed: Zerodium’s highest payout is now $2 million, while another similar company—Crowdfense—offers up to $3 million.
“This makes doing research easier,” Todesco added, referring to the special devices that will be given to researchers. “So there will be more people who find bug chains, and having a more alluring bounty—for someone who’s new to this world—reporting bugs is the most sensible thing to do.”
Have a tip about a data breach or a security incident? You can contact Lorenzo Franceschi-Bicchierai securely on Signal at +1 917 257 1382, OTR chat at lorenzofb@jabber.ccc.de, or email lorenzofb@vice.com
Not everyone, however, is a fan of Apple’s new program.
Katie Moussouris, the security researchers who essentially invented the concept of bug bounties more than 10 years ago while she was at Microsoft, believes Apple is giving researchers the wrong incentives.
“Offense prices will simply increase as a direct result, so this doesn’t ‘compete’ with that market, rather it invigorates it,” Moussouris said in an interview. “They may be sacrificing their own hiring pipeline & possibly even their current internal retention of employees. I hope this does bring out excellent research and new talent, but I fear for the unintended consequences of trying to outbid the offense market.”
Chris Wade, a former jailbreaker and founder of Corellium, criticized Apple’s decision to keep the special devices to a small, select group of researchers.
“Why not just give virtual devices to ALL developers & help arm them with the tools & knowledge to improve platform & app security?” Wade tweeted last week. “Glad to see Apple opening the bounty to all. But how’s it a fair playing field if not everyone has the same tools? No track record of security research? Tough luck no soup for you.”
Apple’s announcements—especially the decision to give researchers special devices—took some by surprise. Earlier this year, a Motherboard investigation revealed that several iOS security researchers were using stolen prototype iPhones to find flaws in iOS. Apple explained that these won’t be developer nor production devices but a new special kind of iPhone made specifically for researchers. The company is calling it the iOS Security Research Device program.

As Forbes put it when it broke the news of Apple’s announcement earlier last week, these special devices are essentially “Hacker-Friendly” phones. Although, perhaps, a better way to look at this is that they are phones that allows hackers to play with them at a lower level of difficulty. If hacking a regular, locked iPhone you don’t own is “GOD MODE,” this is maybe “EASY MODE.”
For years, Apple and the jailbreaking community have been in a sort of a tug of war where both sides learned from each other along the way. Jailbreakers have always been pushing the boundaries of Apple’s walled garden, helping the company fix—or kill as they would say—hundreds of bugs along the way. The jailbreakers didn’t just improve iOS security though, their creative work, such as Cydia—the precursor to the App Store—was later appropriated by Apple engineers. Apple also hired, or at least offered jobs, to many of the most famous jailbreakers and iOS hackers, such as Nicholas Allegra, Comex; and Cyril Cattiaux, aka pod2g.
Subscribe to our new cybersecurity podcast, CYBER.
This article originally appeared on VICE US.