Hackers Trick Venture Capital Firm Into Sending Them $1 Million
Credit to Author: Karl Bode| Date: Thu, 05 Dec 2019 12:56:08 +0000
Security researchers at Check Point say the company has uncovered evidence that Chinese hackers managed to hijack $1 million in seed money during a wire transfer between a Chinese venture capital firm and an Israeli startup—without either side realizing anything was wrong.
The VC firm and the startup, whose names Check Point hasn’t released, reached out to the security firm after the funds failed to arrive. Once Check Point dug into the details, it discovered a man in the middle attack that took a lot of planning and plenty of patience.
After analyzing the server logs, emails, and the computers involved in correspondence between the companies, Check Point noticed some abnormalities. Some of the emails, analysts discovered, had been modified. Others hadn’t even been written by either organization.
After seeing the original email thread announcing the upcoming multi-million dollar seeding fund, the hacker took action. Instead of monitoring subsequent emails by creating an auto forwarding rule (standard practice in traditional attacks), the hacker started by creating two lookalike domains.
“The first domain was essentially the same as the Israeli startup domain, but with an additional ‘s’ added to the end of the domain name,” Check Point said. “The second domain closely resembled that of the Chinese VC company, but once again added an ‘s’ to the end of the domain name.”
From there, the attacker sent two emails with the same subject header as the original email—one posing as the starup’s CEO from the copycat startup domain—and a second sent to the Israeli startup from the copycat Chinese VC firm domain, spoofing the email address of the VC account manager.
That opened the door to a man in the middle attack whereby every email sent by each side of the exchange was in reality sent to the attacker, who then edited the emails to include bogus information and banking details, then forwarded them from each lookalike domain to its original destination.
Throughout this process, the hacker sent a total of 18 emails to the Chinese VC firm and 14 to the Israeli startup ahead of the compromised bank transfer. At one point, the VC account manager and startup CEO scheduled a meeting in Shanghai, putting the hijack at risk. So the hacker sent emails to both sides, making up different excuses to cancel the meeting:
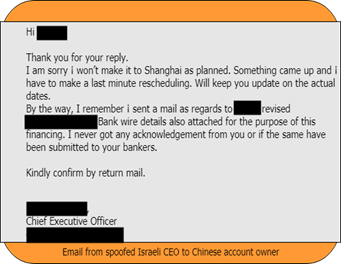
“Patience, attention to detail and good reconnaissance on the part of the attacker made this attack a success,” Check Point said.
After successfully using the man in the middle attack to hijack the funds, the attacker, who still hasn’t been identified beyond his origins in Hong Kong, tried to go after another round of VC investment money. The CFO of the Israeli startup continues to receive one email a month from the spoofed CEO account, urging him to conduct another wire transaction, Check Point said.
The security firm says there’s several things companies can do to avoid a similar fate.
That includes adding a second verification by calling the person who asked for the transfer, keeping audit and access logs for at least six months to ensure the integrity of your email infrastructure, retaining as much evidence as possible when dealing with suspected hackers, and using tools to help spot duplicative, phony domains.
This article originally appeared on VICE US.