How Hackers Are Breaking Into Ring Cameras
Credit to Author: Joseph Cox| Date: Wed, 11 Dec 2019 20:03:55 +0000
Hackers have created dedicated software for breaking into Ring security cameras, according to posts on hacking forums reviewed by Motherboard. The camera company is owned by Amazon, which has hundreds of partnerships with police departments around the country.
On Wednesday, local Tennessee media reported that a hacker broke into a Ring camera installed in the bedroom of three young girls, and spoke through the device's speakers with one of the children.
The family said they had the camera for four days, during which time the hacker could have been watching the kids go about their days.
According to Tennessee local news outlet WMC5, the parents installed the Ring camera in the bedroom of their three young daughters to keep an eye on them. Indoor Ring cameras work with a mobile app that allows users to watch what's happening in real-time and use the speaker to talk through the camera.
“I did a lot of research on these before I got them. You know, I really felt like it was safe,” Ashley LeMay, the girls' mother, told WMC5. A big part of Ring's marketing strategy revolves around making customers feel like their own homes are unsafe, so that they'll turn to surveillance devices to ease those fears.
Do you know anything else about breaking into Ring cameras? We'd love to hear from you. Using a non-work phone or computer, you can contact Joseph Cox securely on Signal on +44 20 8133 5190, Wickr on josephcox, OTR chat on jfcox@jabber.ccc.de, or email joseph.cox@vice.com.
In a video obtained by WMC5 courtesy of the family, you can see what the hacker would have seen: A viewpoint that looms over the entire room from where the camera is installed in a far corner, looking down on their beds and dressers while they play. The hacker is heard playing the song "Tiptoe Through the Tulips" through the device's speakers, and when one of the daughters, who is eight years old, stops and asks who's there, the hacker says, "It's Santa. It's your best friend."
The parents told WMC5 that they hadn't set up two-factor authentication for the device; failing to do so would make it easier for someone to change their password and take control of their account.
Like other IoT smart home camera hackers, this one used the weak password security on the parents' Ring account to access their dashboard and speak directly through the device. A local NBC outlet also reported hackers targeted a Florida family’s Ring camera recently, with the hacker shouting racial slurs through the device.
The news highlights how although a higher level of protection for Ring accounts is available with two-factor authentication, some users are not deploying it, and Ring is not forcing its deployment either, despite a Ring camera potentially allowing a hacker to spy on sensitive conversations or locations.
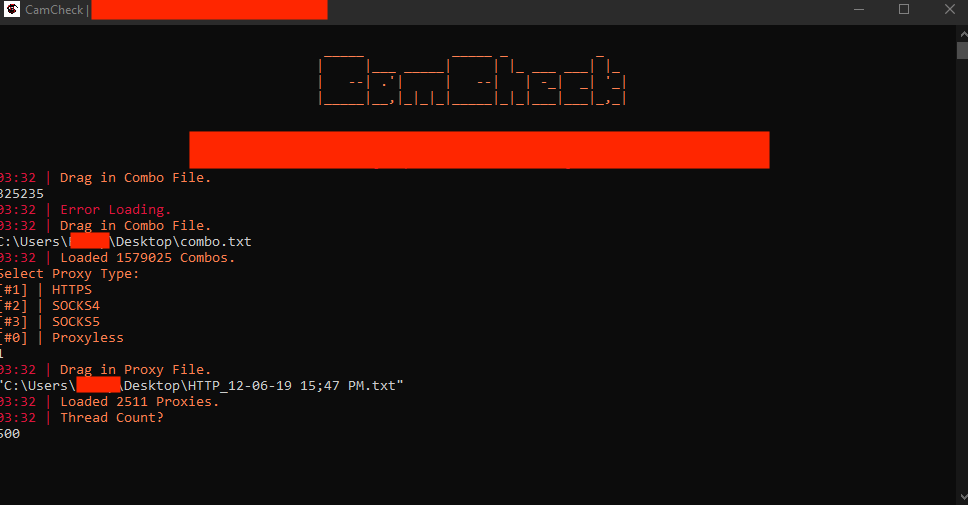
Motherboard found several posts on different crime forums where hackers discuss creating tools for breaking into the Ring accounts which are connected to cameras.
"Ring Video Doorbell Config," one thread on a hacking forum reads. A config is a file used to drive special software for rapidly churning through usernames or email addresses and passwords and trying to use them to log into accounts. Hackers have developed configs for a wide variety of websites and online services, from Uber to Facebook.
The thread title adds that the config has a "High CPM," or high "check per minute," meaning it can test if a username and password allows access to a Ring camera quickly. In a different thread, one hacker is offering a Ring.com checker for $6.

Apparently there is demand for the file, with one user adding on the thread, "I saw multiple people asking for this config."
Another added, "I'd assume you would only use these if you actually we're [sic] planning to break into the persons house."
But, this sort of account can be used to harass, too. In the case of the hacked camera in Tennessee, the girls' father was downstairs during the hack, and came upstairs to stop the camera. Any amount of research into safety of in-home cameras would reveal plenty of examples showing why, for most families, putting a camera in a kids’ room is an unnecessary risk: many smart home cameras and IoT devices have been hacked in the past.
A Ring spokesperson said in a statement, "Customer trust is important to us and we take the security of our devices seriously. While we are still investigating this issue and are taking appropriate steps to protect our devices based on our investigation, we are able to confirm this incident is in no way related to a breach or compromise of Ring’s security.
"As a precaution, we highly and openly encourage all Ring users to enable two-factor authentication on their Ring account, add Shared Users (instead of sharing login credentials), use strong passwords, and regularly change their passwords," it added.
Subscribe to our cybersecurity podcast, CYBER.
This article originally appeared on VICE US.