Black Market T-Mobile Location Data Tied to Spot of a Triple Murder
Credit to Author: Joseph Cox| Date: Wed, 26 Jun 2019 14:36:14 +0000
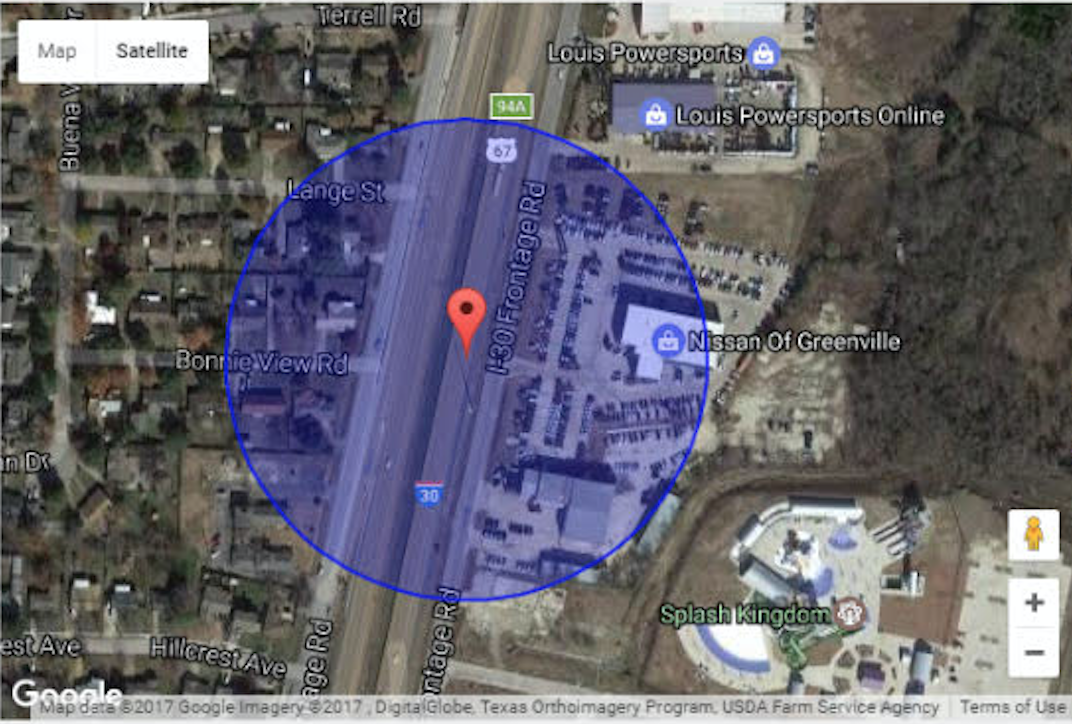
On a hot May evening, two plain-clothed federal agents walked into a Nissan dealership just off the highway in Greenville, Texas, next to a Splash Kingdom waterpark. The agents wanted to apprehend a Roman Hutchinson, who was wanted for failure to appear in court on a first-degree drug charge and who they suspected would be at the dealership.
A family of five was in the building, as well as several employees. The owner of the dealership agreed to let the men wait for Hutchinson.
The two men weren’t really federal agents, however. They were Fidel Garcia and Gabriel Bernal, two bounty hunters illegally posing as law enforcement. Both worked for F.N.G. Security, a bail bondsman firm that had been given the contract to apprehend Hutchinson.
As Hutchinson stood near a desk in one of the dealership’s glass walled offices, the two bounty hunters approached, handguns drawn. One of the hunters grabbed Hutchinson from behind, and attempted to restrain him. Hutchinson pulled a gun from his belt, but dropped it onto the desk, and reached to grab it. Others ran out of the office in a panic.
Twenty gunshots were fired in a span of six seconds, piercing walls and shattering windows. All three men were hit. A cellphone video of the shooting showed bystanders running from the scene, taking cover behind cars inside the dealership, and a woman screaming as the bullets stopped. When police arrived shortly after, all three men were dead.
But someone from afar was tracking the hunters.
In the hours after the shooting, someone with access to a controversial data system looked up the location, or “pinged,” one of the bounty hunter’s phones, pinpointing it to the Nissan dealership, according to data leaked to Motherboard from a company that sold real-time location data of AT&T, T-Mobile, and Sprint customers to bounty hunters.
And in the lead up to the incident on the day of the shootings, that same data access was used to repeatedly ping a phone with a Minnesota area code. Hutchinson was on the run from Minnesota, but Motherboard could not confirm who the phone belonged to or whether the pings were related to the shootings. That phone was pinged eight times on the day of the murder, but was also pinged several times days later.
It is unclear if any phone location data led the bounty hunters to Hutchinson. And naturally, data did not act as an impetus for the murders themselves—that was due to three violent and armed individuals fighting each other during an encounter. The story does, however, show that phone location data tracking services can be used by individuals who impersonate law enforcement, and shoot wildly around innocent civilians, putting them in danger.
On top of illegally posing as law enforcement, the F.N.G Security bounty hunters seemed to have approached the situation recklessly. They didn’t wear bullet-proof vests which were found in their vehicle, Sergeant Adam Phillips, a Greenville Police Department spokesman, told reporters at the time of the shooting.
“For years, I’ve warned that protecting personal data isn’t just about personal privacy, it’s about personal safety,” Senator Ron Wyden told Motherboard in a statement. “Location data is falling into the hands of people who are using it in ways that cause real danger to the public. Americans’ safety is at risk from the shady middlemen and wireless carriers who let anyone with cash in hand track our phones. Americans should be outraged that FCC Chairman Ajit Pai has done nothing to hold the carriers responsible.”
AT&T, T-Mobile, Sprint and Verizon sold their customers real-time location data to middleman companies called “location aggregators.” These aggregators then provided access data to a wide range of other parties, including used car salesman, landlords, low level law enforcement without a warrant, and, as Motherboard revealed, bounty hunters.
In this Texas case, the data of the bounty hunter’s phone first trickled down from a telecommunications company acquired by T-Mobile, according to a screenshot of the phone ping obtained by Motherboard. Then, the data moved through a location aggregator called LocationSmart. From there, LocationSmart sold that access to CerCareOne, a company that operated in secrecy, and which told its clients to not even reveal the company’s existence.
CerCareOne had around 250 bounty hunter and bail bondsman clients for real-time location data, according to previously leaked CerCareOne documents. CerCareOne didn’t only have access to cellphone tower location information, which can pinpoint a device to a range of a few blocks, but also precise assisted-GPS or A-GPS data, which is so accurate it can locate someone’s position inside a building.
The screenshot of the CerCareOne system in action displays the phone’s GPS coordinates as well as its approximate location on a Google Maps interface; the time of the geolocation attempt, and the phone number pinged. According to online records, the phone number belongs to F.N.G. Security, the firm the two bounty hunters worked for, and the coordinates put the phone just outside the Nissan dealership.
Do you know anything else about this case, or about another incident of location data abuse? We’d love to hear from you. Using a non-work phone or computer, you can contact Joseph Cox securely on Signal on +44 20 8133 5190, Wickr on josephcox, OTR chat on jfcox@jabber.ccc.de, or email joseph.cox@vice.com.
CerCareOne worked by giving users an account they could load with credit to then ping phones. The account used to locate the bounty hunter’s phone was registered to a Dan Grable of Nova Technologies, according to another leaked document. Nova Technologies is a firm offering telecommunications services, such as phones for businesses and internet connectivity. Grable had an administrator level account for CerCareOne, another document shows.
The source who provided the CerCareOne documents believes Grable may not have been the only person to be using that account. Grable’s account had been used to locate phones over 4,500 times across several years, according to a list of located phone numbers.
According to a copy of CerCareOne’s terms and conditions obtained by Motherboard, customers were supposed to only connect to the service from up to two predetermined IP addresses. “The subscriber is aware of and agrees to supply to Cercareone.com a maximum of two (2) IP addresses from which access to Cercareone.com will be limited to further ensure privacy and limited access & attests that said IP addresses belong to the subscriber,” the terms and conditions read.
Motherboard found at least two IP addresses used by Grable’s account to connect to the CerCareOne service, which are included in the leaked documents, are associated with Nova Technologies domains. But other pings come from many more IP addresses around the world, including various internet service providers and locations in the United States, and servers in Israel and Lithuania, according to online records. In other words, the use was not being limited to only two IP addresses.
“I think he was reselling it,” the source, who is intimately familiar with the phone pinging underground, said of Grable. “There’s 110 pages, and he’s pinging the same damn number all the time. I think that’s going to be his number; a test number.”
Grable did not respond to emailed requests for comment or voicemails.
“I’ve warned that protecting personal data isn’t just about personal privacy, it’s about personal safety.”
Various parties have filed multiple lawsuits related to the shooting. The McIver family—the mother, father, and three children—have sued the Nissan dealership, F.N.G. Security and Investigations, and U.S. Fugitive Recovery and Extradition, the company that hired F.N.G. The lawsuit describes the bounty hunters as “incompetent and/or reckless.”
“Had any of the Defendants informed the McIver family of Ramon Michael Hutchinson’s presence or Defendant’s intent to apprehend Ramon Michael Hutchinson, the McIver family would not have come to the dealership, or remained on the premises,” a filing from the McIver lawsuit reads.
“If these recovery agents had lived, they would have lost their license and most likely would have done some federal time for impersonating a federal agent,” Valerie McGilvrey, a skiptracer who has bought phone location data in the past, told Motherboard. A skiptracer is someone who finds out where people, often those who owe a debt or a fugitive, are located.
After Motherboard reported about the sale of real-time AT&T, T-Mobile, and Sprint phone location data to bounty hunters in January, each telecom said they were stopping the sale of such data to all third parties.
A T-Mobile spokesperson said they had nothing to add about the Texas shooting incident, but wrote in an email, “that as of February 8, 2019, T-Mobile terminated all service provider access to location data under the program and T-Mobile’s location based services contracts with the location aggregators officially ended on March 9.”
The FCC, which is conducting an investigation into the sale of phone location data, did not respond to a request for comment. As Motherboard previously reported, multiple FCC Commissioners said the agency is withholding information from them about the status of that investigation.
“What I’m hearing, as described in this reporting, is concerning. This story continues a thread of troubling actions by a number of entities throughout the pay-to-track ecosystem. If true, this again points to the alarming public safety implications of making geolocation data available for purchase. It is long past time that the FCC complete any investigations and hold all wrongdoers accountable,” FCC Commissioner Geoffrey Starks said in a statement.
FCC Commissioner Jessica Rosenworcel said in a statement, “The facts surrounding the sale of real-time location data keep getting worse. For just a few hundred dollars, bounty hunters were able to access the location of wireless customers—with chilling results. Meanwhile, it has been more than a year since the first press reports emerged indicating that our wireless location data has been up for sale. But the FCC has done nothing more than suggest it has an investigation. What is the agency hiding? It’s time for the FCC to be upfront about just what is going on and hold those who violated the law responsible.”
This article originally appeared on VICE US.